InterScan Web Security Virtual Appliance
The web has rapidly become a top threat vector for business. In addition to blocking malicious code, inappropriate websites, and targeted attacks, security managers are also
being asked to secure the expanding use of Web 2.0 and cloud-based applications, while reducing overhead and bandwidth costs.
Trend Micro™ InterScan™ Web Security Virtual Appliance is an on-premises secure web gateway that gives you superior protection against dynamic online threats, while providing
you with real-time visibility and control of employee internet usage. Interscan Web Security is also available in the cloud as a service.
Key Benefits
Superior Protection
InterScan Web Security stops threats at the gateway before they ever get to your endpoints. It delivers comprehensive real-time protection against the full scope of web
threats, using anti-malware, the strongest advanced threat protection, URL filtering, web reputation. Interscan Web Security leverages the real-time protection of the Trend Micro™ Smart Protection Network™, ensuring you are protected against new and emerging threats, like ransomware.
Complete Visibility and Control
InterScan Web Security’s granular application control for over 1,000 applications and protocols lets you easily enforce acceptable web use policies. It also provides real-time
central management and monitoring so you can see web use as it happens, enabling on-the-spot remediation. Interactive and customizable dashboards and reports
give you complete visibility of the web usage and data that is most useful to you for assessing your security posture, human resources, and compliance purposes.
Reduced Complexity and Costs
Deployed as a virtual or software appliance, InterScan Web Security Virtual Appliance lets you achieve data center consolidation and standardization. With centralized
management of multiple gateways and native failover and redundancy. the solution makes ongoing management simpler - saving you time and resources.
InterScan Web Security as a Service
Cloud-based protection from Internet threats and control over web usage
The rising sophistication and complexity of web threats, coupled with the new ways your employees work, have eroded the effectiveness of traditional web security solutions. In addition to blocking
malicious code, inappropriate websites, and targeted attacks, security managers also need to protect an increasingly mobile workforce that demands access to new Web 2.0 and cloud-based consumer
applications - all while reducing management and networking costs.
Trend Micro InterScan Web Security as a Service dynamically protects against cyber threats in the cloud, before they reach your users or network. It also delivers real-time visibility and control of
employee Internet usage. Because it is located in the cloud, it protects any user, in any location, on any device - all based on a single policy that moves with the user. It eliminates the need for costly traffic
backhauling or managing multiple secure web gateways at multiple sites. Also, this solution will grow fl exibly with your business - without the need to purchase, manage, or maintain software or hardware.
Cloud-based Web Gateway Security
Protection Points
- Internet Gateway in the cloud
Threat and Data Protection
- Cloud-based applications
- Web 2.0 applications
- Advanced Persistent Threats
- Zero-day exploit
- Malware
- Viruses and worms
- Bots and command and control (C&C) callback
- Spyware and key loggers
- Malicious mobile codes
- Rootkits
- Phishing attacks
- Content threats
Integrates with
Control Manager
Centralized Visibility and Policy Management for Data and Threat Protection
In today’s sophisticated threat landscape, advanced attacks leverage multiple threat vectors, crossing user endpoints, servers, networks, web, and email. You
need to visibility across multiple layers of security to ensure the best possible security protection for your organization. And with the transition to cloud-based
IT delivery models, you need to manage security across on-premises, cloud, and hybrid deployment environments.
Consistent security management will help you bridge the IT silos that often separate layers of protection and deployment models. This type of centralized
approach improves visibility, reduces complexity, and eliminates redundant and repetitive tasks in security administration - all of which make your organization
more secure, and your life easier.
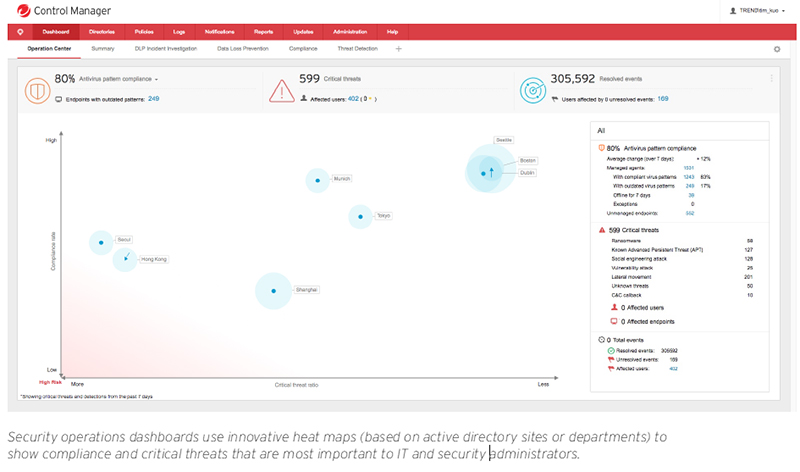
Trend Micro™ Control Manager™ centralized visibility and management solution provides a single, integrated interface to manage, monitor, and report
across multiple layers of security, as well as across both SaaS and on-premises deployment models. Customizable dashboards provide the visibility and
situational awareness that equip you to rapidly assess status, identify threats, and respond to incidents. User-based visibility (based on active directory
integration) enables you to see what is happening across all endpoints, devices owned by your users as well as their email and web traffic, enabling you to
review policy status and make changes across everything the user touches.
And if you do experience a threat outbreak, you’ll have complete visibility across your environment to track how threats have spread. With a better
understanding of security events, you’re more likely to prevent them from reoccurring. Direct links to the Trend Micro Threat Connect database deliver
actionable threat intelligence, which allows you to explore the complex relationships between malware instances, creators, and deployment methods.